WannaCry Malware – the beginning
WannaCry AKA WCry malware uses a known Windows bug in SMB (Server Message Byte) Protocol which is widely used mainly in earlier version of the Windows XP servers. WannaCry is based on the NSA developed exploit known as “EternalBlue“. To understand how the epidemic has started, we here present to you the timeline & the sequence of the events that happened since March
7th March, 2017: WikiLeaks dumped some NSA hacking tools. Unfortunately, EternalBlue was one of them. NSA was using this exploit to hack vulnerable Windows Computers and they never informed MicroSoft regarding this. To protect users, WikiLeaks released the exploits in public so that MicroSoft is forced to release a patch to prevent this exploit. But it did not work very well, you know what is happening right now, right? Well, Mircosoft was very prompt to release a security patch for the exploit (EternalBlue) which is the heart of the WannaCry Ransomware. Despite the end of the support of Windows XP, Microsoft released the patch for XP, Vista and Windows 7. But not all enterprises updated their system hence still vulnerable to the attack. 8th April, 2017: A Hacking group known as “Shadow Brokers” released some more hacking tools and exploits and most of them were “Zero-Day” exploits meaning they don’t have any bug fix just yet. 22th April, 2017: Nasty peoples started doing nasty things with these tools. Some so called hackers started using these exploits and thousands of PC were infected by the malware, zero day tools and viruses. 9th May, 2017: MircoSoft released patches for more than four Zero-Day exploits. 12th May, 2017: WannaCry Ransomeware Hit globally affecting thousands of Corporate offices, Banks, Police departments, Hospitals.
WannaCry Ransomware 101
So, your question now might be, why Ransomware like WannaCry could made it possible to hit more than 99 countries within just two days. Mate, WannaCry replicates itself using SMB protocol in vulnerable Windows servers mainly windows XP, Windows server 2012 etc. Once you copy file from the affected PC or server to another server it becomes infected withing minutes. In this way, this Virus could hit so much computers in a fraction of hours. Few points to be noted:
WannaCry Ransomware is known to affect Windows 10, Windows 7, Windows XP and Windows servers. The Ransomware code name is Ransom:Win32/WannaCrypt. Updated Antivirus may or may not detect it. We have tried different security products and finally we got the winner – THE ULTIMATE RANSOMWARE FIGHTER, ZoneAlarm AntiMalware software can detect the malware and remove it, we tested in a sandboxed Windows XP virtual machine. (It’s free for 30 days). Give it a try. Wannacry ransomware can spread from one computer to another while filetransfer Disinfection is possible but file decryption is yet not possible. Security researchers are trying to find a way but it is not guaranteed to work. Use Antivirus, use a secure VPN while torrenting for the next few days if you don’t want to lose the important documents, photos or files. We recommend you to use these secure VPN service in your Windows PC
WannaCry ransomware affected all versions of Windows
Windows versions that are affected mostly Windows XP, Windows 8, and Windows Server 2003. Some of the affected versions of the operating system (Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8.1, Windows Server 2012, Windows 10, Windows Server 2012 R2, Windows Server 2016) which did not receive the security patch released by Microsoft in March are also vulnerable.
WannaCry Ransomware – What happens to your computer after getting hit
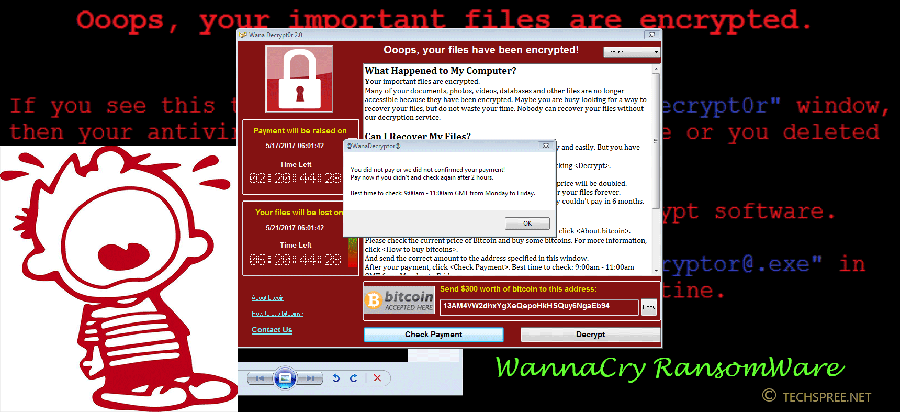
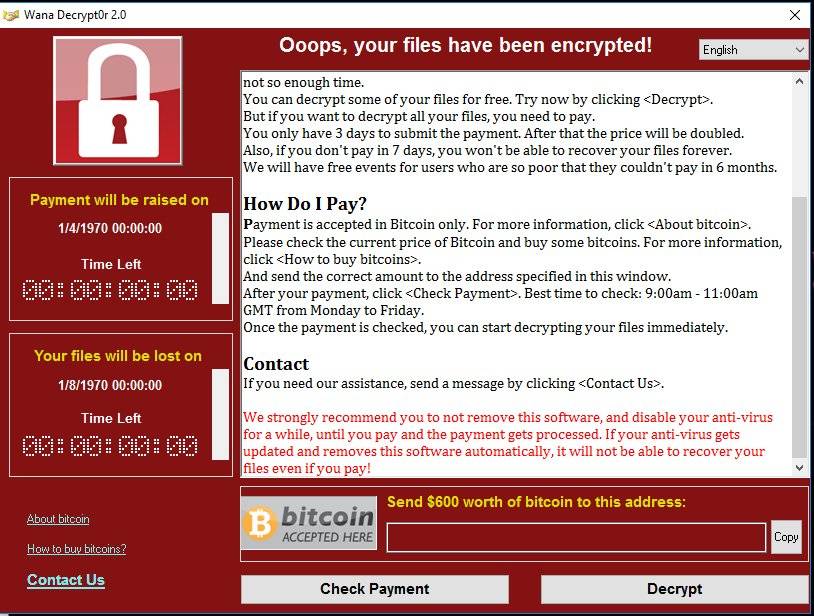
First you will notice that a single popup window is being opened with a bitcoin address to pay than ransome within 6 hour time frame. It will usually ask for 300$+ worth of bitcoin. If you delay the payment, the amount will rise as the time passes by. WannaCry ransomware encrypts your all important files with a private key which is known to only the hacker. Without this key (passcode) you can’t decrypt the files. So hackers ask for money for the private key that is used to encrypt your data. If you want to access your important files you must pay the ransom. You will see the below WannaCry banner in homepage:
Don’t pay the Ransom – Creators of WannaCry Ransomware can’t be trusted
Although you send the payment, the creator of this ransomware may or may not give you the passcode necessary to unlock files. Given that numerous hackers group are involved, getting back your files is solely in the hand of the hacker himself. As reported by BBC News, it is not recommended to send the bitcoin payment because the transaction is irreversible.
How to protect yourself from WannaCry ransomware attack
Buy Heimdal PRO software and install it along with a good Antivirus program.
Few things you can do to avoid the WannaCry ransomware infecting your Windows Computer or servers:
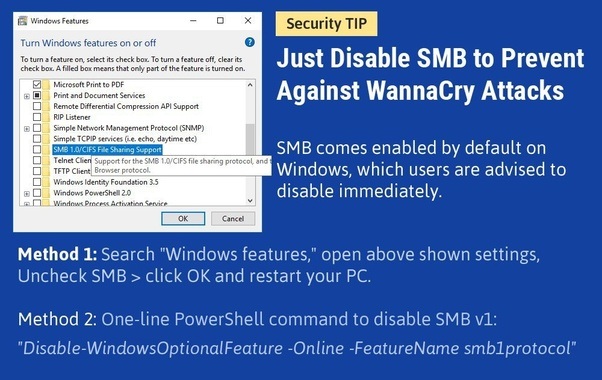
Use a Good Antivirus / Internet Security, or Antimalware software. We recommend Heimdal Ransomware Pro software to use along with Antiviurs. I have reviewed Heimdal Pro software. You can read review from here. Don’t open attachments sent by unknown users into your email inbox. Update your Windows Computer as soon as possible. Don’t download files from unknown source. If you torrent a lot get a torrent VPN. Isolate the infected computer and don’t connect it with any LAN or WiFi to prevent spreading. Disable SMB protocol